Think you can ignore quantum computing? Think again.
CIO
MARCH 27, 2024
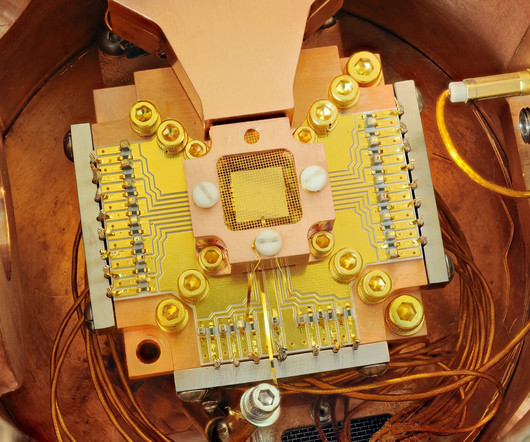
In 1994, American mathematician Peter Shor developed quantum algorithms to factor integers and solve the discrete logarithm problem. When run on a big enough quantum computer, these algorithms will be able to crack all the public key crypto systems we rely on today for privacy. The impact will be felt globally.
















































Let's personalize your content