The Role of Data Structures and Algorithms in Software Development
Smart Data Collective
APRIL 15, 2024
Explore how data structures and algorithms power software development. Learn key concepts and best practices for efficient coding.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
 Algorithm Related Topics
Algorithm Related Topics 
Smart Data Collective
APRIL 15, 2024
Explore how data structures and algorithms power software development. Learn key concepts and best practices for efficient coding.

Smart Data Collective
OCTOBER 16, 2022
AI technology has helped investors make automated trades with algorithmic trading. Algorithmic trading for short-selling with AI Technology. But, there’s another way to do it, which is algorithmic trading which relies on AI algorithms. Algorithmic trading short-selling solutions. from 2022 to 2027.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Smart Data Collective
FEBRUARY 9, 2022
Using the DirectX analytics interface can enable you to pick out important trading insights and points, which simplifies algorithmic trading. For example, when your trading algorithm makes losses or a particular threshold or condition is met. Let’s say for a few weeks or several months to determine the times it was underachieving.

Smart Data Collective
AUGUST 1, 2022
However, some have started using AI to automate many trading decisions with algorithmic trading. Algorithmic trading refers to a method of trading based on pre-programmed instructions fed to a computer. The AI algorithms that it uses can identify trading opportunities most humans would have missed. from 2022 to 2027.

Smart Data Collective
APRIL 3, 2022
One of the ways to make money through the use of AI technology is with algorithmic trading. What is algorithmic trading? One such avenue for making money is algorithmic trading. Automated trading (also known as “algorithmic trading”) works by using AI algorithms to perform trades. Advantages.

Smart Data Collective
OCTOBER 8, 2021
Learn how genetic algorithms and machine learning can help hedge fund organizations manage a business. This article looks at how genetic algorithms (GA) and machine learning (ML) can help hedge fund organizations. Genetic algorithm use case. As well as bolster investor confidence and improve profitability. Final thoughts.
Smart Data Collective
SEPTEMBER 14, 2022
Despite going through fluctuations over the last decade, high-frequency algorithmic trading (HFT) remains popular on the market. What Is High-Frequency Algorithmic Trading and How Does AI Help? It utilizes programs that constantly monitor the market and make split-second trading decisions based on an algorithmic approach.

SpyFu
JULY 23, 2024
As an SEO or marketer, knowing how search engine algorithms work can give you a competitive edge. In this post, we'll break down the algorithms of major search engines: Google, Bing, DuckDuckGo, and YouTube. What is a Search Engine Algorithm? That’s where their individual algorithms come in.

Smart Data Collective
JUNE 8, 2022
They have been a successful algorithmic trader for the past 17 months. This trader never imagined that their life would be completely transformed by becoming an algorithmic trader. What is algorithmic trading and what role does data analytics play? This automated trading with rule-based trading bots is algorithmic trading.

Smart Data Collective
FEBRUARY 8, 2021
Algorithms and learning machines can make it all sound very complicated, but there isn’t too much to it, and you don’t have to be any sort of expert to understand how machine learning algorithms are used within this realm and how they predict trends and changes. How does this work, and what are these algorithms predicting?
CIO
MARCH 27, 2024
In 1994, American mathematician Peter Shor developed quantum algorithms to factor integers and solve the discrete logarithm problem. When run on a big enough quantum computer, these algorithms will be able to crack all the public key crypto systems we rely on today for privacy. The impact will be felt globally.

Zoominfo
NOVEMBER 15, 2021
Instead, use a lead-scoring algorithm that analyzes win rates against data points from ideal customer profiles (ICPs ). Use these five attributes to create a lead-scoring algorithm to rank the webinar leads. For example, imagine you have 100 qualified leads from a product webinar.
Timo Elliot
APRIL 8, 2024
That already means that you’re at the mercy of the search algorithms that decide or not to show your content to prospects. And the “prospect” may not even be a person: it could be an AI agent or algorithm that has been delegated the task of finding the best product for the need. How will that be possible?

CIO
OCTOBER 13, 2023
AI researchers help develop new models and algorithms that will improve the efficiency of generative AI tools and systems, improve current AI tools, and identify opportunities for how AI can be used to improve processes or achieve business needs.

SpyFu
MAY 1, 2023
To discover, categorize, and rank the billions of websites that make up the internet, search engines employ sophisticated algorithms that make decisions on the quality and relevancy of any page. These decisions are guided by an algorithm. Understanding how an algorithm works helps you create content that ranks better for each platform.

CIO
JUNE 19, 2024
In short, members won’t share data or algorithms but there will be a collective system allowing expertise and learning to be shared. Some academic medical centers (AMCs) and healthcare organizations already have processes in place to test and approve AI algorithms. This will be done through a “federated AI outcomes registry.”

CIO
SEPTEMBER 22, 2023
But as quantum computers become more powerful, they will be able to break these cryptographic algorithms. Secure private keys derive from mathematical algorithms — the Rivest-Shamir-Adleman (RSA) algorithm is a common one — that are impossible to reverse-engineer and hack. Mastercard’s project focuses on the latter method.

Zoominfo
FEBRUARY 7, 2018
Earlier this year, the ‘original’ social network made headlines with the announcement of their updated News Feed algorithm. In today’s post, we give you the scoop on Facebook’s new algorithm, and we prepare you for the impending change. How is Facebook’s new algorithm different? Keep reading! What is the reason for this change?

CIO
JUNE 26, 2024
It was probably two years before the algorithm was truly ready to go into production,” says Donovan Reid, associate director of information services applications at Penn Medicine, and four years went by before the system finally was ready for production last year. The system didn’t come together overnight, though. “It

CIO
JANUARY 26, 2024
The ability of all SDVs — combustion-based, hybrid, and fully electric — to feed data up to the cloud provides developers with a plethora of unique opportunities to build algorithms that optimize, and in some cases, automate, vehicles.
CIO
FEBRUARY 10, 2023
On the cutting edge of predictive analytics techniques are neural networks — algorithms designed to identify underlying relationships within a data set by mimicking the way a human mind functions. Clustering algorithms, for example, are well suited for customer segmentation, community detection, and other social-related tasks.

CIO
JUNE 3, 2024
By analyzing vast datasets and identifying patterns, AI algorithms generate insights that drive informed decision-making and spur creative solutions to complex problems. Moreover, AI supercharges a culture of innovation by providing developers with powerful tools to explore new ideas and experiment with novel approaches.

CIO
AUGUST 11, 2023
How natural language processing works NLP leverages machine learning (ML) algorithms trained on unstructured data, typically text, to analyze how elements of human language are structured together to impart meaning. An NLP algorithm uses this data to find patterns and extrapolate what comes next.

CIO
JUNE 13, 2023
On one, privacy advocates are building clever algorithms that reveal just enough information to pass through whatever identity check while keeping everything else about a person secret. Chance of succeeding: The basic algorithms work well; the challenge is social resistance. Or maybe just ten or five or one?

CIO
JANUARY 19, 2024
Generative AI algorithms can expand the range of available character features, allowing gamers to tailor appearance, apparel as well as contextual behaviors based on gameplay. Algorithms driven by generative AI can provide texture synthesis and create realistic, high-quality textures for game objects and environments.

CIO
NOVEMBER 1, 2023
One of the first use cases of artificial intelligence in many companies, including both Michelin and Albemarle, was predictive maintenance, which at its most basic level is an algorithm trained on data collected by sensors. To fill the gap, many companies complement the real data with synthetic data.

CIO
SEPTEMBER 12, 2023
Everyone is still amazed by the way the generative AI algorithms can whip off some amazing artwork in any style and then turn on a dime to write long essays with great grammar. Generative AI algorithms are still very new and evolving rapidly, but it’s still possible to see cracks in the foundation. The stock prices are soaring.

CIO
AUGUST 10, 2023
We have nesting algorithms to help with that. AI and sophisticated numerical analysis algorithms are used to minimize material waste, which adds up to big money when large volumes are involved. Computer aided design (CAD) tools, which are often used to model the irregular shapes, can feed the models to the nesting algorithms.

CIO
JULY 2, 2024
For example, Netflix’s 2009 $1 million algorithm contest succeeded but the algorithm wasn’t used due to integration issues and business model changes. Having a superior solution doesn’t guarantee business acceptance. Technology adoption depends on timing and maturity. While crucial, innovation should be practical.

CIO
MAY 8, 2024
AI-powered data integration tools leverage advanced algorithms and predictive analytics to automate and streamline the data integration process. Anomaly detection Anomaly detection algorithms can identify unusual patterns in data that might indicate errors, fraud, or emerging trends.

CIO
NOVEMBER 28, 2023
Wholesale moves off of the mainframe are fraught with risk and ever-increasing costs, but the analytical capabilities of the cloud are full of opportunity and potential for innovation, fueled by AI and ML algorithms. The answer is mixed—or, more accurately, hybrid.

CIO
OCTOBER 16, 2023
Predictive AI uses advanced algorithms based on historical data patterns and existing information to forecast outcomes to predict customer preferences and market trends — providing valuable insights for decision-making. Predictive AI utilizes machine learning algorithms to learn from historical data and identify patterns and relationships.

CIO
JULY 20, 2023
Algorithmic retail With fast-changing customer preferences and a rise in competition, retailers are increasingly turning to AI to help them solve complex problems and make faster decisions. By putting algorithms to work on big data collected from diverse sources, retailers can intelligently predict what customers will buy and in which order.

CIO
MAY 10, 2024
The legislation requires companies that conduct business in Colorado to disclose to the state’s attorney general “any known or reasonably foreseeable risk of algorithmic discrimination, within 90 days after the discovery or receipt of a credible report.”

CIO
SEPTEMBER 8, 2023
The primary prediction algorithm in production is ordinal logistic regression and different techniques are used to deal with the class imbalance problem (stratified sampling, SMOTE, etc.),” Swanson says. Completed algorithms are shared via Amazon Web Services S3 infrastructure with the SC EMR IT team.
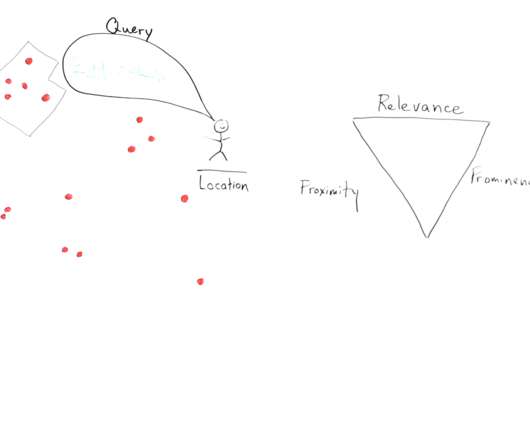
Moz
DECEMBER 5, 2019
In this week's Whiteboard Friday, renowned local SEO expert Mary Bowling lays out the three factors that drive Google's local algorithm and local rankings in a simple and concise way anyone can understand. This is Mary Bowling from Ignitor Digital , and today I want to talk to you about the local algorithm. Video Transcription.

CIO
JUNE 3, 2024
Although he does not anticipate the disappearance of GPUs, he says future AI algorithms will be handled by a mix of CPUs, GPUs, and AI co-processors, both on-premises and in the cloud. Many organizations have adopted sustainability goals, which power-hungry AI algorithms make it difficult to achieve.

CIO
MAY 8, 2024
In about six months, Expion’s two AI developers created ExpionIQ Advisor, a tool that uses linear regression, multiple algorithms, and custom-built AI models to automate prescription RFPs. The two teams also conducted focus sessions to validate the logic and finalize the model, he adds.

CIO
JUNE 18, 2024
Laying the foundation for artificial consciousness The quest to build artificial consciousness is ambitious, as maximizing the groundbreaking algorithms introduces a whole new set of hardware infrastructure requirements—the first of which is compute power.

CIO
AUGUST 9, 2022
This is critical, ensuring algorithms deliver valuable insights, analytics and support increased automation. Nevertheless, most organizations face growing problems around users’ trust in algorithms. In order to overcome this issue, the applications running AI algorithms must be designed to build confidence in the outcomes.

CIO
JUNE 25, 2024
If you build it as an independent application, you might, over time, replace the customer experience that you’re delivering without having to change the fraud detection algorithm.” All that could be built outside of your core customer service application.

CIO
APRIL 30, 2024
These images are then analyzed using machine learning algorithms to detect oil spills and pollutants. “A recently published patent application demonstrates this usage, describing the deployment of drones in sub-surface terrain to capture images.

CIO
MARCH 5, 2024
Venkatesh Natarajan, former chief digital officer of Ashok Leyland, said that achieving a completely unbiased model is challenging due to factors such as data biases and inherent limitations of AI algorithms. Google, too, has its own algorithms for detecting AI-generated content but has not made any announcements on this front.

CIO
JANUARY 26, 2024
Carnegie Mellon says the department’s research strategy is to maintain a balance between research into the cure statistical-computational theory of machine learning, and research inventing new algorithms and new problem formulations relevant to practical applications.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content