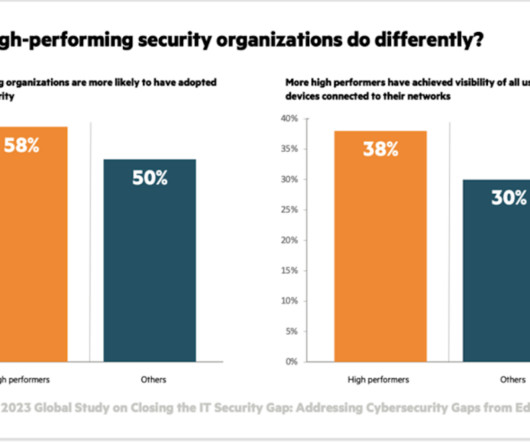
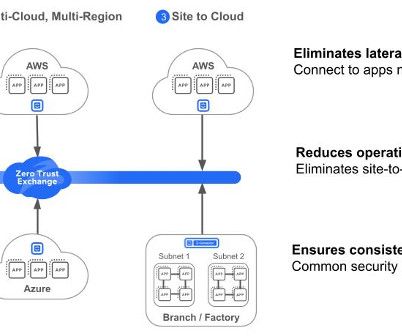
3 business benefits of stronger security using Zero Trust principles
CIO
MARCH 6, 2024
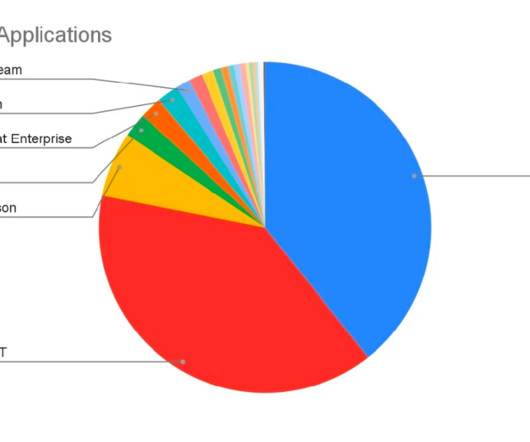
Historically, these weren’t designed with security in mind. OT assets are highly vulnerable to attack because they don’t have built-in security, traffic isn’t encrypted and there’s low visibility into their functioning. Security is paramount for the core infrastructure that supports manufacturing and industrial operations.












































Let's personalize your content