CIOs are worried about the informal rise of generative AI in the enterprise
CIO
AUGUST 30, 2023
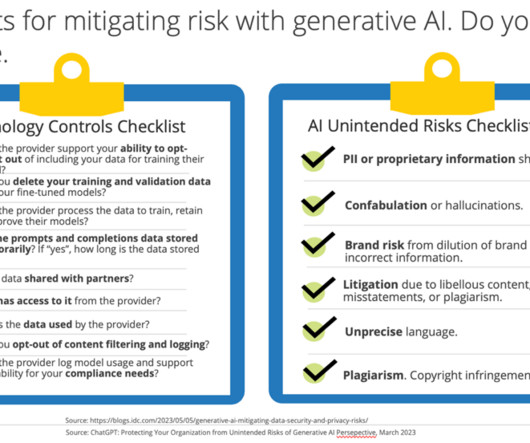
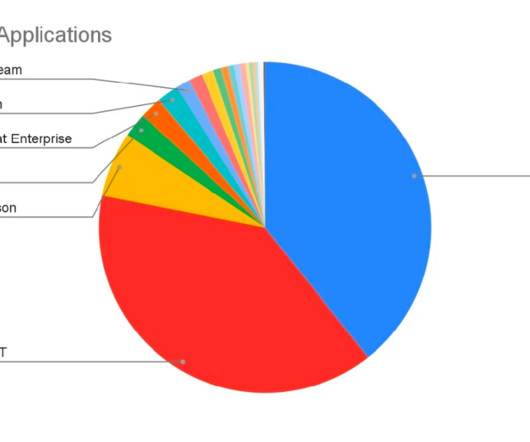
Organizations are seeing a dramatic rise in informal adoption of gen AI – tools and platforms used without official sanctioning. A CISO at a major marketing software firm worried about this explicitly, stating, “The real risk is that you have unintentional data leakage of confidential information. Privacy leaks?















































Let's personalize your content