Implications of generative AI for enterprise security
CIO
OCTOBER 10, 2023
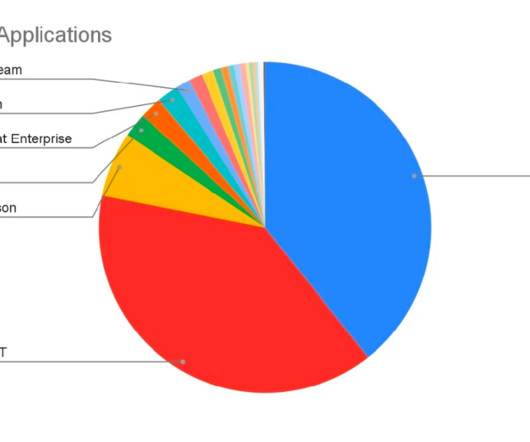
A technology inflection point Generative AI operates on neural networks powered by deep learning systems, just like the brain works. But unlike human learning, the power of crowd-source data combined with the right information in Generative AI means that processing answers will be light years faster.














































Let's personalize your content