Implications of generative AI for enterprise security
CIO
OCTOBER 10, 2023
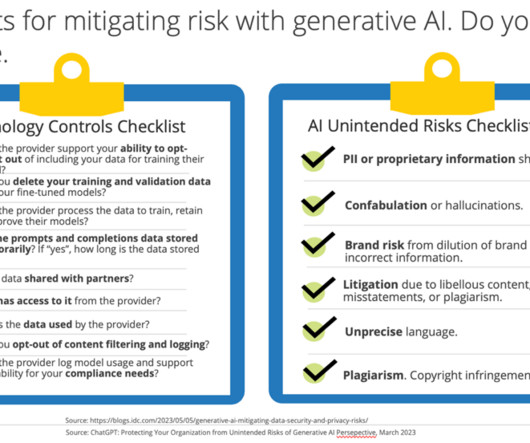
Providing sensitive information to Generative AI programs such as personally identifiable data (PII), protected health information (PHI), or intellectual property (IP) needs to be viewed in the same lens as other data processor and data controller relationships. It inspires awe and unease — and often both at the same time.












































Let's personalize your content