Gaining an AI advantage: Not all AIs are created equal
CIO
DECEMBER 21, 2023
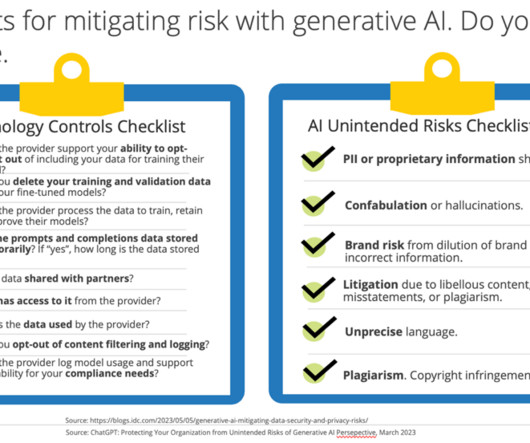
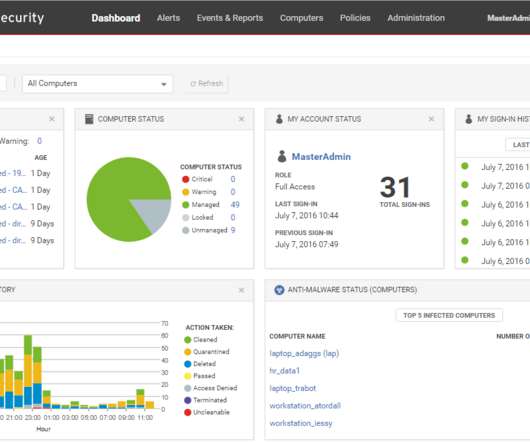
By analyzing large volumes of clean data from various sources, such as network traffic logs and user behavior patterns, AI can correctly identify anomalies and potential security breaches that may go unnoticed by traditional security measures. Real-time processing is key to keeping systems secure and ensuring swift incident handling.














































Let's personalize your content