Generative AI: 5 enterprise predictions for AI and security — for 2023, 2024, and beyond
CIO
OCTOBER 25, 2023
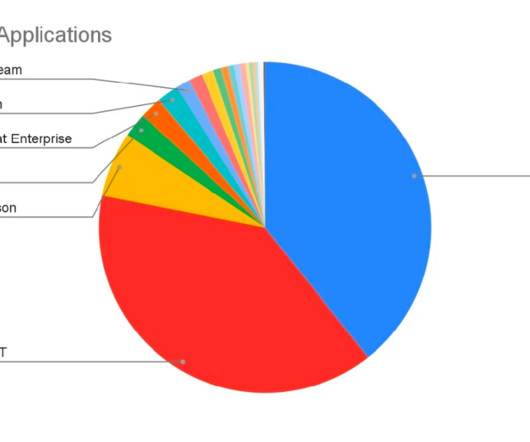
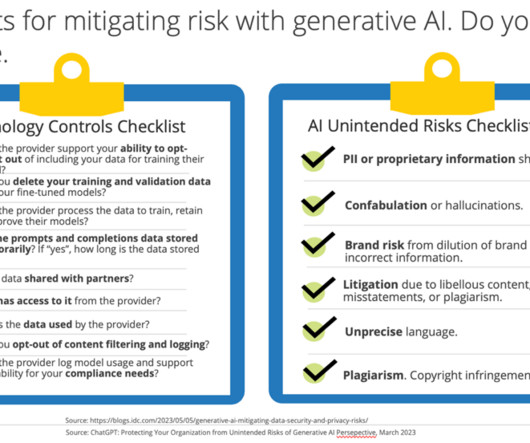
As new AI use cases continue to emerge, it is likely that we will see enterprises adopt AI — not merely in leveraging generative AI chat tools, but as a core driver of business that can create competitive differentiation. The data privacy and security risks of AI applications themselves Not all AI applications are created equal.














































Let's personalize your content