Generative AI and the Transformation of Everything
CIO
OCTOBER 24, 2023
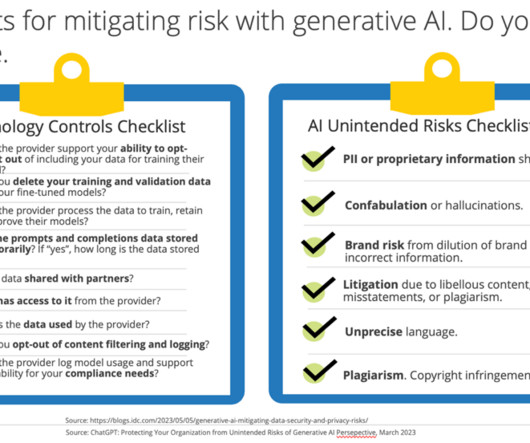
Another major concern is copyright infringement and intellectual property (IP). It starts with the business policies of the organization — with education and setting a foundation to understand and recognize the risks that generative AI entails. Information loaded into it becomes data that any other subscriber has access.














































Let's personalize your content