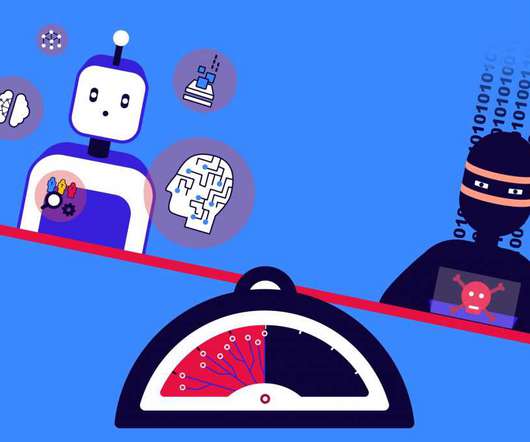
2 Innovations That Can Tip the Balance in Cybersecurity
CIO
JANUARY 13, 2023
This includes hunting and deep, high-end analysis. It does not include traditional policy and legal landmines such as personally identifiable information, protected health information, intellectual property, or surveillance-related data. Any other approach will never keep pace with the speed and scale of modern cyberthreats.









Let's personalize your content