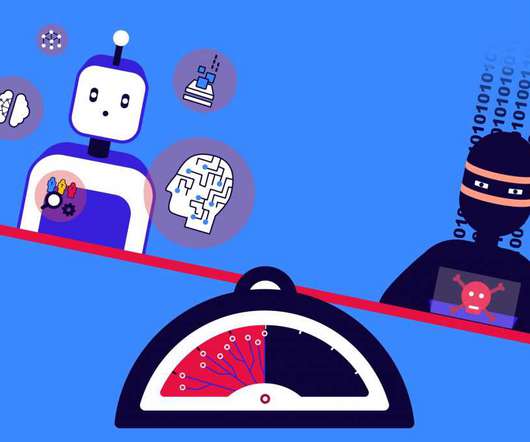
2 Innovations That Can Tip the Balance in Cybersecurity
CIO
JANUARY 13, 2023
It does not include traditional policy and legal landmines such as personally identifiable information, protected health information, intellectual property, or surveillance-related data. Eliminating or reducing the advantage that cyber offense has over defense is critical to creating a more stable cyberspace.










Let's personalize your content