Radically simplify and expand Zero Trust to cloud workload
CIO
DECEMBER 21, 2023
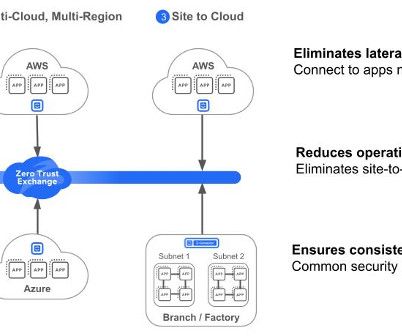
The public cloud imperative For many organizations, regardless of size or industry, the public cloud has become an essential resource for critical operations. The latest advancements include: Real-time resource discovery enables native integration with AWS to automatically locate VPCs, subnets, and EC2 resources.














































Let's personalize your content