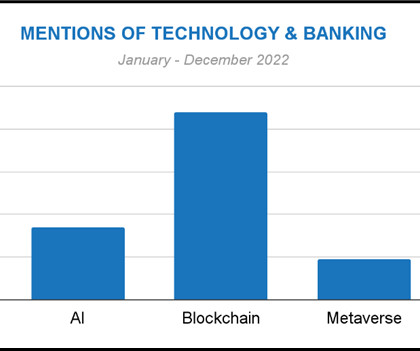
Banking on customer experience and security via technology-based innovation
CIO
JULY 20, 2023
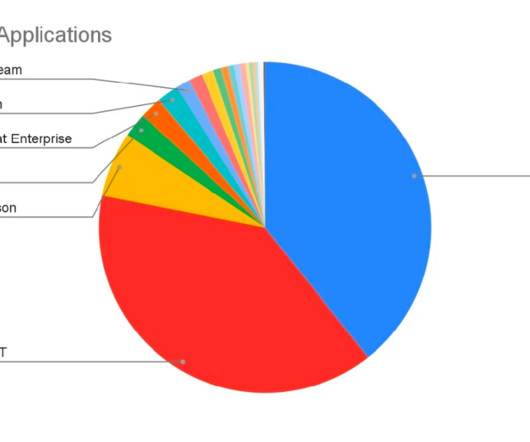
Since then, automation has filled the gap in improving customer experience and security. Customer experience and security But as in most industries, customer expectations and security challenges continue to grow along with technological advances. Security and privacy.














































Let's personalize your content